How you respond to any incident can have a dramatic effect on the overall outcome and its potential on going impact. Over this two-part series Foregenix will look to answer the question – “How well will you respond when it really matters?” covering Incident Response and the often-overlooked gap that is ‘Intrusion detection’ or as we like to call it ‘Incident Readiness.’
All too often we see that businesses are on the receiving end of a heavy fine for leaking cardholder data, and with GDPR just on the horizon the loss of any personal data could also be subjected to business-changing fines. The number of companies reporting breaches continues to grow, month on month, confirming what most companies are now beginning to realise “It’s not if but when!”
Unfortunately, no security system is 100% infallible; as the old saying goes “where there’s a will, there’s a way” – and hacking is no different. Your environment must be permanently secure, whereas a determined attacker only has to be successful just the once. Taking protective measures, such as firewalls and anti-virus, are of course vital, but it’s time we shift the paradigm and move the spotlight onto detective controls.
Think of it this way: if a burglar were to get past the lock on your front door, what would tell you that they were inside your home? Without additional security measures (a burglar alarm for example) you wouldn’t know there was an intruder until you find your possessions have been stolen. Securing your network works in a similar way.
It’s reported that the majority of data breaches (53%) are detected by third parties; not the company itself, long after the incident has occurred. Within the Payment Card Industry there are a number of these third-parties (Card Brands, Acquirers, and Issuers) all looking to identify fraud, and in these instances, the cash-out from an attack can be obvious and swiftly identified.
The cash-out is the moment an attacker profits from an attack, ex-filtrating valuable data which they use to benefit from, normally with a monetary reward.
But for environment breaches where cardholder or financial data is not the target of the attacker, recent studies have shown the average time between an attack and third-party detection is 320 days. Whereas for those who self-detect, the average time between attack and detection is 56 days. From the Foregenix archives the longest detection time we’ve seen to date was in excess of 6 years!
A hacker could be in your environment, siphoning away important information (financial or otherwise) for almost a year before it’s picked up by a third party. Reducing the time it takes to detect the attack can have a big impact on the on going reputational damage to your business, as well as the resulting implications – including fines.
Examples that could be used to reduce the detection time of an incident are:
- Active log monitoring
- Detailed auditing throughout the environment
- Monitoring and analysis of user and system activity
- Anti-Virus systems
- File Integrity Monitoring (FIM)
- Honey pots (such as Canary)
- Third party Intrusion Detection Systems (IDS)
Once you have selected an intrusion detection solution to deploy, consideration should be made to where you position your alarms to catch and track any intrusion. The key here is “Defence In Depth” – meaning IDS should be placed in layers throughout the environment, not just as single shell on the periphery; thus giving the greatest opportunity to identify and track any potential intruder. Whether you deploy all or some of the above, the most important factor is that the IDS needs to be set to raise alarms when they detect something.
Once detected, these alarms must be responded to immediately by experienced, qualified staff. An IDS can’t conduct investigations and so human interaction is imperative, to conduct an initial assessment of the alert.
Below we have an example of a typical incident timeline from the perspective of the victim and the attacker.
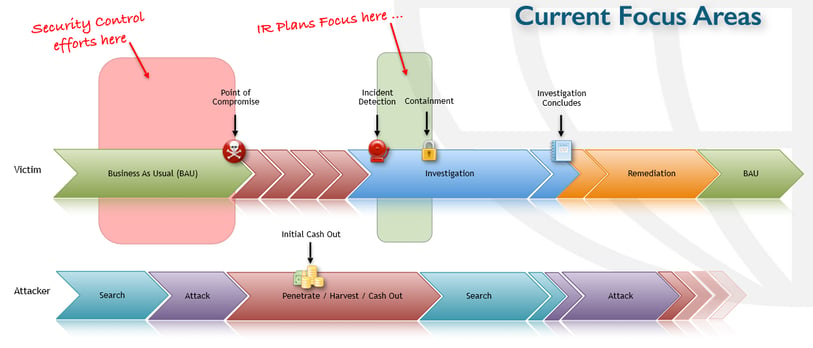
As you can see, the areas currently focused on by organisations are the initial security controls (firewalls, multi-factor authentication, etc) and the Incident Response (IR). What’s missing is the systems in place to detect the attack whilst it’s in progress. Preferably as early as possible.
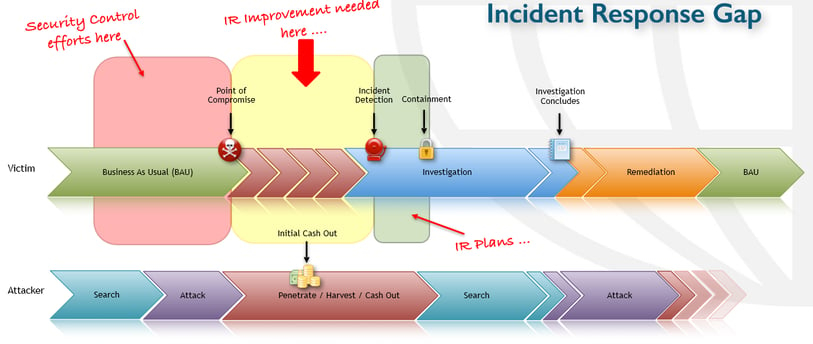
The idea is that the quicker you can detect a breach, the quicker you can contain, remediate, and return to business as usual with minimal cost or damage to your reputation. The average cost in the UK to resolve a cyber attack per type and the amount of time it takes to rectify them are as follows:
- Malware:£1.57 million – 6.4 days
- Web-based attacks:£1.52 million – 22.4 days
- Denial-of-service (DoS) attacks:£1.31 million – 16.8 days
- Malicious insiders:£960,000 – 50 days
- Malicious code:£960,000 – 55.2 days
- Phishing and social engineering:£960,000 – 20 days
- Stolen devices:£700,000 – 14.6 days
- Ransomware:£520,000 – 23.1 days
- Botnets:£260,000 – 2.5 days
The longer it takes for you to resolve an incident, the more money it’ll cost you, but being able to detect that incident in the first place is the key to reducing the effects of the aftermath.
Next in our incident readiness series, we will look at bridging the gap between the initial point of intrusion and the instigation of an effective incident response plan.
