
Major corporations spend hundreds of thousands of pounds and in some cases employ teams of people dedicated to manage and ensure the security of their environment. But as a small eCommerce merchant, who is responsible for the security of your environment? In most cases, small eCommerce businesses elect to outsource all of their website’s development to professionals specialising in eCommerce environments, but should the developers be responsible for the cybersecurity as well as the development and management of the environment?
The argument over who should take responsibility for the environment’s security is one of the biggest reasons that card breaches happen on eCommerce websites. The security element had slipped into the gap between the merchant and the developer – with it becoming neglected over time. Such simple measures such as user account management, password rotation, log monitoring and reviewing of intrusion detection alerts could identify early signs of an attack, potentially preventing a breach altogether.
In many cases security is over looked all together until it is too late, with no consideration as to how an attacker may view your web site. It is an unfortunate reality that those you trust to build and manage your website likely have never been taught to adopt a security mind set and to view their work through the eyes of someone with malicious intent. For example, the developer manages any unknown page request by serving the web applications default 404 error page. What's wrong with that? Well, to any genuine user - nothing. For the attacker on the other hand, it provides vital information about your environment.
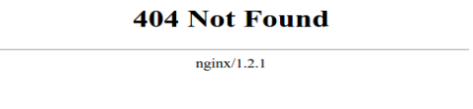 Illustration 1: Default 404 return page for Nginx web application
Illustration 1: Default 404 return page for Nginx web application
The attacker now knows the web application you're running and the version number. Time to access the hackers book of knowledge; “Google”.
Some of the most common oversights
During many of the forensic investigations conducted by Foregenix, it is simple oversights in the security stance of the eCommerce environment that provide the initial attack vector and, ultimately, lead to the breach.
Some of these are:
- Web-based administration access located on the default URL or uses one that can be easily guessed. The log-in page is also left publicly accessible.
- Error pages returning useful information to attackers.
- Unused default applications are left available, for example RSS feeds or file upload functionality.
- Shared user credentials.
- User credentials provided to third-parties and are left active when not required.
- No user management policy; obsolete user accounts remain active, and a policy of least privilege not adopted.
- No password management policy, including no consideration to password complexity or rotation.
- Patching and maintaining an up-to-date environment.
- No vulnerability testing.
- No monitoring of log files or intrusion detection systems.
- Lack of appropriate log files.
- Lack of intrusion detection systems, such as File Integrity Monitoring, Web Application Firewall etc.
PCI DSS clearly puts the responsibility for an environment’s security with the merchant, along with the responsibility for ensuring that any third-party also operates within a PCI DSS compliant manor. But as a small eCommerce business this can be a daunting and confusing prospect in that you have little or no knowledge or experience. As such, many small eCommerce only merchants are putting their trust in development companies who offer “the complete eCommerce package”. Unfortunately, security is too often overlooked, not considered or falls into the gap between the developer, the merchant, and any other third-party, such as the hosting provider. By the time security is at the forefront of everyone’s minds, it is already too late. An attacker has had access to the environment, card data has been stolen and your acquiring bank is demanding that you undergo a Payment Card Industry Forensic Investigation (PFI).
Security can be expensive with little-to-no visible return which, for a small merchant where every penny counts, can be a real dent in company profits. However, the risk of looking the other way in the hope that it won’t happen to you could be a very costly approach, with the possibility for fines levied by the card schemes for data breaches, in addition to the cost of a forensic investigation and potentially full PCI DSS security audit. Further to this, May 2018 sees the introduction of General Data Protection Regulation (GDPR) and likelihood of further large fines for losing personal data. In some cases, the costs of dealing with a data breach has caused companies to cease trading. Is that still a risk worth taking?
So, where do you go from here?
The first step I would recommend is accepting the fact that your environment requires security and that, as a merchant, you must be responsible for ensuring this. I would then strongly advise having a conversation with your web developer and potentially your hosting provider to identify any gaps in security and security management of the environment. Depending on the knowledge and experience of yourself and your third-parties, you may be able to address any gaps yourself.
Unfortunately, small eCommerce only sites are becoming easy pickings for attackers, with the volume of attacks increasing this is becoming a very profitable crime. Automated scans run by attackers are able to scan the WorldWide Web, identify commonly used eCommerce platforms, such as Magento, providing a list of potential victims. Platforms such as Magento are so extensively used that their vulnerabilities and exploits are widely documented, including the locations of default URLs for such pages as administration log-in screens. Security does not have to cost the earth and even simple steps can take you out of the sights of the attackers. With so much cardholder data available, attackers will target the weakest links or lowest hanging fruit. Don't let that be you!
Questions to consider and discuss with your developer
- Who is responsible for the overall security of my eCommerce web site?
- Do we have Anti-Virus running on the host server?
- If so, who maintains this, and when was it last updated?
- Who acts on any alerts raised?
- Who is responsible for patching the environment and keeping it up-to-date?
- When was this last done?
- How often is the environment patched?
- How do we know if patches are released, and how quickly are they implemented?
- Is the environment (website) tested for common vulnerabilities, if so how?
- Do we use default error pages or custom ones?
- Are our web-based administrative log-in pages publicly accessible?
- Are there any default applications that we are not using, if so, have these been disabled?
- Who manages user accounts for the host server, and administration access to the eCommerce environment?
- Are obsolete user accounts removed?
- Are user credentials shared?
- Do we use a policy of least privilege for all users?
- Who manages passwords for administration access to the host server and eCommerce environment?
- What is the password complexity policy?
- What is the password rotation policy?
- Is two factor authentication in place?
- Is logging enabled? What are we logging; web access logs, administration access and change logs?
- How long are logs maintained?
- Who has access to the log files and can they be manipulated?
- Who monitors the logs for suspicious activity?
- Are any intrusion detection systems in place?
- If so, who monitors any alerts, and how often?
- Is the environment protected from all known threats? Are we implementing a firewall on the host server and a web application firewall on the eCommerce site?
- What processes and procedures are in place to respond to a security incident?
If you are interested in checking the security stand-point of your web site please use our free website scanning tool - WebScan or contact info@foregenix.com for further information
Subscribe to our Blog

Benjamin Hosack
Benj Hosack is a Director and co-Founder of Foregenix Limited. Foregenix is a specialist information security business delivering services in Forensics, PCI DSS, PCI P2PE, PA-DSS and information security solutions within the Payment Card Industry. Our technologies are designed to simplify security and PCI Compliance. Specialties: Cardholder Data Discovery - defining and reducing PCI DSS Scope / PA-DSS / PCI DSS / P2PE / Account Data Compromise Investigations. We are specialists in the Payment Card Industry and work with all types of companies in the payment chain (Acquiring banks, Processors, hosting providers, web designers, merchants, systems integrators etc).
See All Articles