Understanding Payment Card Industry Data Security Standards (PCI DSS) and how it relates to a small to medium-sized eCommerce business is the first challenge for most businesses trying to becoming PCI DSS Compliant. With this article we hope to simplify what you need to know, what you need to do and why it is important.
⚠️ UPDATE (December 2024)
This article was originally published in July 2016 and reflects PCI DSS v3.2.1 requirements. Since then, PCI DSS v4.0 has been released with critical new requirements for SAQ A merchants:
- Requirement 6.4.3: Client-side script management for payment pages
- Requirement 11.6.1: Payment page tampering detection mechanisms
- Requirement 11.3.2: External vulnerability scanning now mandatory for SAQ A
These requirements became mandatory on April 1, 2025. For detailed implementation guidance on these new requirements, see our comprehensive guide to PCI DSS v4.0 Requirements 6.4.3 and 11.6.1 for eCommerce merchants.
The core principles in this article remain valid—security must come before compliance—but current SAQ A merchants must also implement these additional v4.0 controls.
So what is the PCI DSS?
The Payment Card Industry Data Security Standard (PCI DSS) is a set of security controls based on security best practice, designed and developed by the major card payment schemes (Visa, MasterCard, American Express, JCB, Diners and Discover) to enhance the security of cardholder data and thereby reduce the risk of data compromise and fraud on a global basis.
Who does the PCI DSS apply to?
The PCI DSS applies to all organisations that store, process or transmit payment cardholder data. For online businesses, if you can accept a payment card transaction for goods or services on your eCommerce website (even if you hand the transaction off to your payment processor), then the PCI DSS applies to you.
How to validate your PCI DSS compliance:
There is a single Payment Card Industry Data Security Standard which details all the controls required to be in place in any Cardholder Data Environment (CDE). The CDE is the part of a business that handles all payment card data.
Depending on the type and size of your business, you may be asked to either validate your compliance with the PCI DSS via a Self Assessment Questionnaire or to have an Onsite Assessment by a Qualified Security Assessor (QSA). Merchants (a business that accepts payment card transactions) are categorised into one of four levels. Level 1 merchants being the largest and requiring an onsite assessment, through to level 4 merchants who are required to validate their compliance via a Self Assessment Questionnaire.
Visa and MasterCard clearly define the merchant levels here:
PCI Compliance for eCommerce Websites
We assist many eCommerce businesses in either understanding what they need to do to become PCI Compliant, or in helping them get their business back following a compromise (hack) of their website where they have had their customers' cardholder data stolen.
Unfortunately there is a lot of misunderstanding about security and compliance, which often results in businesses thinking they are secure because they have completed a PCI DSS Self Assessment Questionnaire (SAQ) when, actually, they are not.
So with this understanding and experience, we always advise our clients to focus on security first – do that well and PCI Compliance will come naturally.
This article is aimed at the small to medium sized eCommerce businesses, generally categorised as a level 3 or level 4 merchant in PCI terms.
Security First
Through misinformation, misunderstanding, or competing business priorities, many eCommerce businesses complete their Self Assessment Questionnaire, conduct basic vulnerability scans, and believe they are secure. That is until they receive the call from their bank saying they've been compromised and need to spend thousands on a forensic investigation to find out why.
Unfortunately, it seems that a lot of businesses assume that they are secure because they have outsourced their payments, have passed their scans and completed a SAQ for their bank. And that is where their security strategy stops.
Perhaps they're slightly justified in thinking that their web developer agency/IT solutions provider is taking care of the technical detail – however, as we talk about in a different blog post, it is generally NOT the case when it comes to security.
Website security is a key part of running a successful eCommerce business and requires careful consideration, a good strategy and a competent team to ensure that a website remains secure. An insecure website with an outsourced payment model can still be hacked and lose payment card data – as you can read in our blog articles.
Self Assessment Questionnaires
The PCI DSS is a comprehensive standard and the assessment process is detailed, lengthy and can be costly. Fortunately for smaller businesses, the PCI Security Standards Council (the body that manages the PCI DSS) has recognised this and have a number of
 Self Assessment Questionnaires that smaller businesses can complete to validate their compliance with the PCI DSS.
Self Assessment Questionnaires that smaller businesses can complete to validate their compliance with the PCI DSS.
Which SAQ applies to your eCommerce Business?
For companies that accept eCommerce payment card transactions (but don’t accept card-present payments from customers in person) – then there are two SAQs that could apply to your business. Depending on how you handle payment card transactions, you could complete either:
- SAQ A, or
- SAQ A-EP
SAQ A
This Self Assessment Questionnaire is for eCommerce or mail order/telephone order merchants that meet the following description:
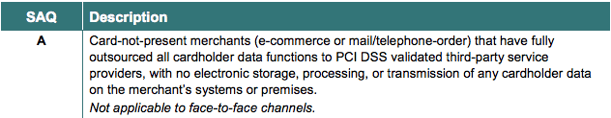
Websites utilising an iFrame or Hosted Payment Page are able to complete SAQ A. In these payment acceptance models, payment data is input directly into a form or page hosted by the eCommerce website’s payment service provider. A few examples of payment options that meet SAQ A criteria are:
- Ingenico - E-Commerce and Alias Gateway solutions
- Verifone – Hosted Payment Page
- Optomany – axept Checkout
- MasterCard (DataCash) – Hosted Payment Solution
- Stripe - js and Checkout
- PayPal – Hosted Pages
The SAQ A asks merchants to confirm that they meet this criteria and then focuses on passwords, access control measures, physical security and policies and procedures. It is a relatively short questionnaire and often once completed, most businesses don’t generally think about security until the following year when they are asked to complete the SAQ again.
SAQ A Merchants can still get hacked
Unfortunately, this is where a lot of eCommerce businesses fall victim to attackers resulting in expensive, disruptive forensic investigations and penalties from the card schemes.
Just because the questionnaire is short and simple, it does not mean that the rest of the PCI DSS is no longer of importance. The SAQ A is merely the method by which a merchant validates compliance with the PCI DSS.
So, when the merchant’s website technology (Magento, Drupal, OS Commerce etc) is identified as having a security vulnerability and the web developer does not get the website patched quickly, an attacker may have a opportunity at hacking the site (and they often do).
Need some more convincing?
Have a read of the following blog articles – most of these were written following forensic investigations of numerous small to medium eCommerce businesses that had been hacked and had their customers' payment card stolen from them – even though they had been outsourcing their payments and did not think that they had to worry about securing the transaction:
- Alert: Major UK Payment Service Provider iFrame Man-In-The-Middle Breach
- PCI Compliance, SAQ A & the Hacked Website. Does tick box compliance ensure security?
- Malware Alert: iFrame Interception attack affecting websites with outsourced payment models
- Magento Malware Alert: Malicious Client Side Javascript
- Magento Malware: Credit Card Hijack – Malicious Javascript Alert
The Real Cost of a Compliance-Only Mindset
Through our forensic investigations, we consistently see eCommerce businesses that believed completing SAQ A meant they were fully protected. Their experience typically follows this pattern:
**Before the breach:**
- SAQ A completed and validated with their bank
- Payments outsourced to a PCI DSS compliant service provider
- Using redirect or hosted payment pages (meeting SAQ A criteria)
- Assumption that web developer was handling all security aspects
- No awareness of ongoing security risks
**The wake-up call:**
- First notification comes from their acquiring bank about suspected compromise
- Many don't believe it initially—"but we're PCI compliant!"
- Discovery that thousands of payment cards have been stolen
- Facing expensive forensic investigations (£3,000-£5,000+)
- Business disruption, potential penalties from card schemes
- For some businesses, this event becomes catastrophic
**The gap that attackers exploit:**
Here's what most merchants don't understand: SAQ A validates compliance with specific PCI DSS requirements, but it doesn't make your website secure. When your website technology (Magento, WooCommerce, etc.) has a security vulnerability and isn't patched quickly, attackers gain access to your site. From there, they can:
- Modify your payment page redirect to intercept card data
- Inject malicious JavaScript into your checkout process
- Install persistent backdoors for ongoing data theft
- - Manipulate iFrames to capture payment information before it reaches your PSP
Your payment service provider is secure. Your redirect is configured correctly. You've completed SAQ A. But none of this protects you if your website itself is compromised.
**The forensic evidence:**
In our investigations, we've seen eCommerce businesses attacked every 5 minutes on average. It's not personal—attackers have indexed the top eCommerce websites by platform, and when a zero-day vulnerability is announced, they know exactly which sites to target. Your website is being scanned multiple times daily, probed for weaknesses, tested for exploitable vulnerabilities.
The businesses that get breached aren't necessarily doing anything wrong from a compliance perspective. They're simply treating PCI DSS as a checkbox exercise rather than a security strategy.
The message is:
If you want to have secure payments, you need to secure your website.
SAQ A-EP
SAQ A-EP is for eCommerce merchants who meet the following criteria:
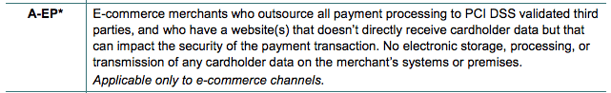
To simplify this paragraph from the PCI SSC a little, this means that direct post, JavaScript, XML or any other techniques which involve the eCommerce merchant’s server to process and/or transmit cardholder data to the payment service provider are required to complete SAQ A-EP.
Essentially, the eCommerce merchant is capturing the payment data in a form and passing it on to their payment service provider’s API. Generally we see this form of payment more frequently in larger eCommerce environments.
Most of the payment service providers mentioned earlier have options that fall into this category, such as:
- Ingenico – Direct Link (API)
- Verifone – XML-based Web Services
- Optomany – axept Gateway
Always check with your payment service provider about how the integration works and whether you meet SAQ A or A-EP definitions - and then check with your Qualified Security Assessor.
SAQ A-EP asks considerably more questions than SAQ A about the security of the web server environment, making it slightly more challenging to complete. But, in asking the more in-depth questions, it could easily be argued that it makes those eCommerce businesses think about their security in a more detailed way than SAQ A and therefore they tend to be more secure.
Security and PCI DSS
So now that you know which SAQ - A or A-EP - applies to your business, we would urge you to not stop at simply answering the questions presented to you without thinking through the following:
- Who manages and maintains your website?
- Do you have an agreement for them to maintain the security of your website?
- What exactly do they provide you in the way of website security?
- What happens if your business gets hacked? Be prepared for the worst.
- Do you have Cyber Breach Insurance?
Working with a secure, PCI DSS Compliant payment gateway is the first step in securing your client transaction data. The next step is to ensure that your website is secure, because if your website is not secure, it is easy for criminals to steal from you.
Need Help Navigating PCI DSS v4.0 for Your eCommerce Business?
If you're an eCommerce merchant transitioning from SAQ A v3.2.1 to v4.0 requirements or determining whether you qualify for SAQ A versus SAQ A-EP under the current standard, our QSA-certified team can provide guidance. Learn more about our PCI DSS compliance services for merchants.
Subscribe to our Blog

Benjamin Hosack
Benj Hosack is a Director and co-Founder of Foregenix Limited. Foregenix is a specialist information security business delivering services in Forensics, PCI DSS, PCI P2PE, PA-DSS and information security solutions within the Payment Card Industry. Our technologies are designed to simplify security and PCI Compliance. Specialties: Cardholder Data Discovery - defining and reducing PCI DSS Scope / PA-DSS / PCI DSS / P2PE / Account Data Compromise Investigations. We are specialists in the Payment Card Industry and work with all types of companies in the payment chain (Acquiring banks, Processors, hosting providers, web designers, merchants, systems integrators etc).
See All Articles