Recent forensic investigation case work being managed by our team has identified a growing e-commerce threat – a new breed of malware being used to compromise online businesses and steal their customers’ personal data – especially focusing on payment card data.
How does this malware work?
This malware threat is a new derivative of the Mage.jpg malware and what makes it different is its ability to conceal itself and it’s harvesting activity from website owners/managers.
This malware resides within the app/mage.php file and monitors every request to the website for valuable data, collecting payment details such as name, address, credit card number, expiry date, CV2, usernames, passwords and so on.
Then, using both encoding and Public/Private key encryption, it encrypts the harvested data and stores it on the website for later collection.
How is the harvested data stored?
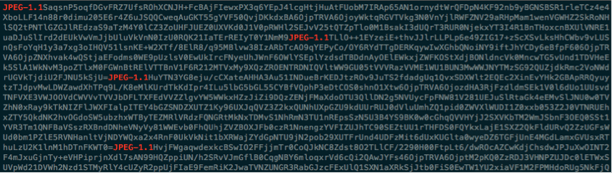
The encrypted, harvested data is being stored in what masquerades as a legitimate image file, in recent cases we have seen both “.jpg”, and ”.png” files being used, with random filenames (the original version of Mage.jpg named the harvesting files "Mage.jpg"). Inside the example harvest file screenshot below you can see the data, highlighting each individual entry to the file. The file is made up with the following pattern “JPEG-1.1<Encoded data(Encrypted-Password|Encrypted-Data)>” which is repeated throughout the file. Each entry representing a set of compromised transaction details.
Time Stamp Changes
Every time new captured data is added to the harvest file it checks to see if the harvest file exists, if so it will write the newly captured data to the file and then amend the file's "modified" time stamp to a predetermined value (a value that is embedded within the malware code), this prevents the modified time from changing in order to prevent victims from being alerted to unusual changes.
How is this malware getting onto victim systems?
In every case that forensic team has dealt with, this new version of Mage.jpg malware is being found on systems that have been compromised through an unrelated system vulnerability or weakness. Once the attackers gain access to the web root they generally deploy web shells and are then able to operate with ease - loading malware as needed, changing files, adding users, changing permissions and so on. For additional information on the web shells commonly associated with hacked e-commerce websites, visit: http://blog.foregenix.com/webshell-alerts-filesman-and-p.a.s.
What data is being harvested?
The malware is collecting all POST data submitted to the victim site, this can be anything from leaving a comment to entering payment details such as credit cards numbers and billing addresses. Once the harvested data has been retrieved by the remote attacker, the harvesting file is truncated leaving minimal traces to raise suspicions, but waiting for the next site user to present their information.
What can you do?
The Reactive Approach
1. First of all, check if this malware is present on your website. Here are a few commands you can run to detect key identifiers. From your document root run the following:
find . -type f -exec egrep -Hl "md5\(md5\(microtime\(\)\)\.rand\(\)\)|\@file_put_contents\([^,]+,'JPEG-1\.1'\.base64_encode\([^\)]+\),FILE_APPEND\)" {} \;
2. Secondly, if these commands indicate that you may have the malware on your website, contact our forensics team. Your speed in reacting can make a huge difference in the potential liabilities facing your business – you need to shut the attack down as quickly as possible, ascertain the damage and contact your bank to minimise the liabilities.
We can help you. This is what we do for hundreds of businesses each year.
The Proactive Approach
You can very easily protect your online business against these sorts of attacks by implementing a simple four-step defence-in-depth strategy utilising our FGX-Web Protect solution.
We offer a 7 day free trial, which will help you to quickly identify any issues and get your online business protected.
If you need help with understanding the technology or alerts, you have our team on hand to support you and to ensure you have a secure online business.
