Part 1 of 2 – Introduction and Background
NfSen is an open source netflow data capture and analysis module which can be used as a standalone product, and is also integrated into AlienVault’s USM/OSSIM security monitoring software.
Exploring Zero-Day Vulnerabilities in NfSen and AlienVault OSSIM
During a penetration testing engagement for one of our clients, Foregenix discovered a zero-day vulnerability in NfSen. The zero-day allowed remote code execution as root, resulting in a total server compromise.
Figure 1 is an example of one of the vulnerabilities, exploited by Foregenix, in order to execute a command on the underlying operating system:
- The blue annotation in the screenshot indicates the input that Foregenix used to trigger the vulnerability.
- The red annotation shows the resulting operating system command responses, which were echoed back to the web browser.
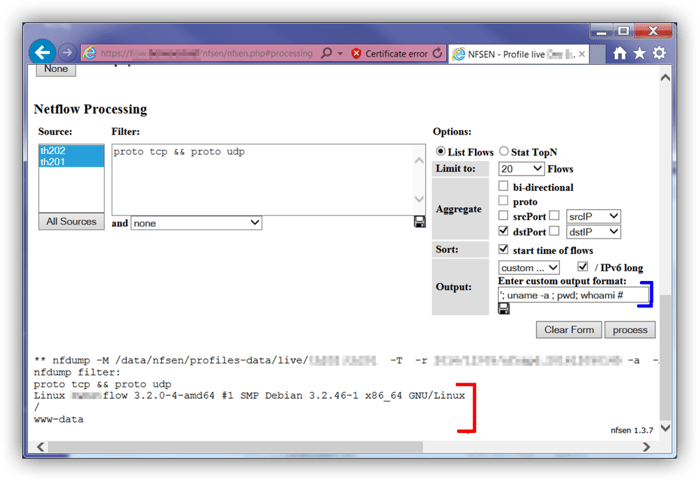
Figure 1 - Remote code execution. The “www-data” response masks the fact that the actual user is root
Wanting to ensure both our clients and the community at large could become fully protected, Foregenix launched an investigation to identify NfSen affected versions by this zero-day vulnerability and whether AlienVault’s USM/OSSIM products were also affected, as NfSen is integrated in them. The investigation showed that all versions of NfSen were vulnerable; however, current versions of AlienVault’s USM/OSSIM were not affected, due to a security measures that AlienVault had already implemented to protect their custom code-branch of NfSen against a cross-site scripting vulnerability.
Foregenix investigation, which consisted of manual web application testing and source code analysis, has revealed three additional zero-day vulnerabilities, all of which affected the current version of NfSen and AlienVault’s USM/OSSIM. These further vulnerabilities allowed remote code execution as root and local privilege escalation to root, giving an attacker full control in each case.
In summary, the vulnerabilities discovered were as follows:
- 2 x Remote root exploits – OS command injections with different vectors
- 1 x Local privilege escalation
- 1 x Failure to drop privileges
Foregenix number one priority is protecting our clients, which was a challenge in this case due to the lack of available fixes for these vulnerabilities. As such, Foregenix needed to contact the vendors as part of our responsible disclosure policy.
Foregenix then liaised with the developers, provided the required information and assistance to help them reproduce the issue and develop the necessary patches. Going the extra mile, our team also assisted in testing the patches. Testing was a success, and as a result, we were able to notify our client with the fix before the patches were publicly available. Subsequently, Foregenix released the CVE details so that other organisations could learn about the vulnerabilities and protect themselves.
The associated CVE numbers and other references are as follows:
CVEs: CVE-2017-6970, CVE-2017-6971, CVE-2017-6972, CVE-2017-7175,
Exploit-DB:
https://www.exploit-db.com/exploits/42314 (CVE-2017-6972, CVE-2017-7175)
https://www.exploit-db.com/exploits/42305 (CVE-2017-6970)
https://www.exploit-db.com/exploits/42306 (CVE-2017-6971)
Vendor references:
https://sourceforge.net/p/nfsen/news/2017/01/nfsen-138-released---security-fix/
https://www.alienvault.com/forums/discussion/8698
https://www.alienvault.com/forums/discussion/8325
In the future a more technical post will be released to explain the vulnerabilities in-depth.
