Spring is finally upon us and after a long, gruelling winter; lambs are frolicking, daffodils are sprouting, and hackers are still breaching websites. It’s time to revisit your website security and make sure you’re taking the necessary measures to protect yourself and your customers.
Magento is one of the most popular eCommerce platforms out there with 260,000 merchants currently using it as their online storefront. It’s the most popular for good reason. It’s a flexible, adaptable, platform with the largest offering of customised and tested extensions.
Due to it’s popularity, unfortunately, it has become a target for hackers worldwide. As part of our latest research, we scanned 217,946 Magento websites. Of those, 86% were running unpatched software (we believe these could be hacked in under an hour) and 4500 are hacked and losing customer card data as we speak.
The majority of issues among hacked websites were:
- Out of date software
- Websites with default settings
- Lack of security monitoring
- Weak passwords
Magento are aware of the threats facing their customers, and take their security seriously, but there’s only so much they can do if you’re not being proactive. Aside from the initial financial costs of a data breach, there’s also long lasting reputational damage that can cripple a small business. Staying secure online has never been more important, so lets take a look at how you can help keep your storefront free of malicious activity.
1. Stay patched and keep your Magento updated
Magento bring out new versions and patches for its software on a regular basis. These often include fixes for discovered holes in the software such as bugs and security issues. With each new update, Magento will release patch notes detailing what exactly they have changed and why. Whilst this is great for people who want to know what’s new, it also gives hackers the information they need to exploit older versions of the software.
A quick search of ‘CVE Details’ (a security vulnerability data source) tells us that as of January 1st 2017 (updated September 6th 2017) there was a flaw that allowed third parties to attack outdated versions of Magento. Details here:
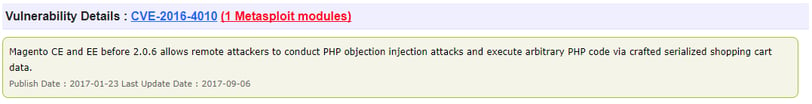
PHP Objection Injection can allow an attacker to perform all kinds of malicious actions, such as Code Injection, SQL Injection, Path Traversal and Application Denial of Service. This is just from one quick search and I’m certain there will be more out there if you look hard enough.
Question: How do you avoid the above mentioned exploit?
Answer: By keeping your version of the Magento store up to date.
Keeping your software up to date with the latest versions is an easy and quick way to help remain free of unwanted activity on your website. Patches are released every few months and so keeping an eye on the Magento Security Centre for updates will benefit you. The security centre also provides you with Magento security news, best practices and the option to report any security issues you may find.
2. Monitor for unprotected cardholder data
Most eCommerce domains are set up to handle transaction data securely. This is often using a secure payment service from a payment service provider. However, considering that payment cardholder data is highly valuable to a criminal, many websites continue to fall victim to payment cardholder data theft.
These attacks usually involve malware, changes to a website and unusual system behaviour. All of which should be detected with other layers of defense software. However, if perpetrators do manage to evade detection and are able to extract transaction data, it’s usually stored in a file somewhere on your website to harvest later. Often this card data is awaiting extraction unencrypted.
A regular scan for PAN numbers (the long card number on the front of a payment card) in file systems and databases will identify the exposed data and alert you to the issue. Once it’s been made known, you can take steps to clear your website of malware and any unencrypted card information.
As a side note: if you are using an API link to access payment card data and then forward it to your payment service provider, then I would strongly recommend the payment method is changed. You should move to a redirected payment model, either with an iFrame, or even better, a fully redirected page. (And you still need to make sure your website is secure)
3. Utilise your firewalls
An unprotected web server potentially leaves customer card data and other sensitive information vulnerable to a breach. Most hosting providers will supply their clients with a basic firewall, which whilst useful, will not completely protect the website.
A basic network firewall performs what is known as Stateful Packet Inspection (SPI) and is configured to only inspect the basics of any packet. These include: the destination IP address, port number, whether it belongs to a valid session and information located within the packet header and footer.
An SPI firewall does not inspect the payload of a packet and so cannot prevent attacks such as innocuous web browsing, spyware, adware, Trojans or other malware. An SPI firewall will simply control the incoming traffic. It will not protect against application based attacks such as SQLinjection, Cross Site Scripting, or Brute Force attacks. These are regularly seen by the Foregenix forensics team as the root cause of most eCommerce website breaches.
 A Web Application Firewall (WAF) however, is able to determine the exact intention of the HTTP(S) content at the application level filtering out illegitimate traffic based on rule sets. Unlike conventional firewalls it will inspect the payload within a packet. This makes the WAF much more versatile when protecting your environment.
A Web Application Firewall (WAF) however, is able to determine the exact intention of the HTTP(S) content at the application level filtering out illegitimate traffic based on rule sets. Unlike conventional firewalls it will inspect the payload within a packet. This makes the WAF much more versatile when protecting your environment.
WAF’s are often used to monitor the information being input into a webform or search tool. The WAF will be able to detect whether the data being input is legitimate or malicious. For example, dates, post codes and product information may all be legitimate. But if you put code into that form with the intention of manipulating the application, you can sometimes find exploits that will give you direct access to the database that’s contained behind it.
Research from our forensic team over the past 10 years found 95% of all hacked e-Commerce businesses have fallen victim to one of three major threats;
- SQL Injection
- Application Vulnerability Exploits
- Injected code (malware)
A properly configured and managed WAF will protect you against these attacks. A WAF will also provide a site with “virtual patching” when a zero day vulnerability is released.
4. Change the URL for your Admin Page and Magento Connect Manager
By default, the Admin Page for your Magento website will be yourdomain.com/admin. If you leave this unchanged, it makes it easy for it to be accessed by a third party. Whilst this isn’t enough to breach your website, from here they can launch a Brute Force attack to crack your password and access your storefront.
If you need assistance in creating a unique URL for your Admin Page, Magento have released a helpful guide on doing so. Click here to find out how.
The path to your Magento Connect Manager should be moved from it’s default location at /downloader, to a path that is already protected from public access. You should rename it to something more obscure, for example: var/myhiddendownloader. When access to the Magento Connect Manager is required to upgrade or install an extension then the directory can be moved back.
5. Restrict access to your Admin Panel and Magento Connect Manager
You should limit access to your Admin Panel and Magento Connect Manager to known IP addresses only. You can do this by using a .htaccess file. Placing the following code into your .htaccess file will restrict your admin page access. The .htaccess file will need to lie within the root of the /admin directory and the /downloader directory.
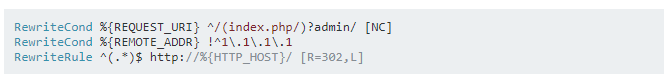
Taken from Magento’s question and answer forum ‘Stack Exchange’.
Keep in mind that 1.1.1.1 and above would be populated with the IP address you would be using to access the admin panel/Magento Connect Manager.
Additional password protection could also be added by creating a password file within the var/ directory.
It’s also worth noting that many of the attacks we see against eCommerce environments involve adding an unauthorised user account to the data. I recommend that a review of all user accounts in the database is conducted.
6. Disable Directory Indexing
Disabling directory indexing makes it more challenging for criminals to work out how to access your Magento core files. Similar to the strategy suggested for adding a custom path for your Admin Page, it makes it more challenging for criminals to traverse your website. If they’re unable to find chinks in your armour, they are more likely to move on to easier targets.
When a web server reveals a directory’s contents, the listings could contain information that is not meant for public viewing. Often web administrators assume that if there are no hyperlinks to these documents, they will not be looked for, or found. This assumption is incorrect.
7. Create backups of your websites
Backups should be automated, systematised and kept offsite. Having an up to date backup could mean the difference between your website being taken down for days, or being back up and running quickly. Having a clean backup of your website makes the rebuilding process after an attack easier, meaning your business can carry on as usual, much faster.
Backing up your website is relatively simple and can save you from a potentially crippling situation. If you’re unsure of how to create a backup of your website then I would suggest searching online or contacting your hosting provider.
8. Deploy File Change Monitoring
One of the first signs you’ve been compromised is when files start being introduced, changed or deleted. In the daily management of a busy site, an attacker’s small file changes can easily be missed without the technology to monitor them. Monitoring changes taking place on your website is an essential step in detecting malicious activity and can be done very effectively.
Foregenix’s own File Integrity Monitoring system within our FGX-Web solution will usually run a scan every four hours. The data is logged and then a notification is sent to the client if a file has been changed.
The FIM logs are especially useful for when we detect something like a webshell. It means we can load up the log and identify exactly when a change was made. It also allows us to see which other files were created around the same time. This paints a full picture of what you’re dealing with, so it can be completely eradicated.
9. Malware detection
Malware is a term used to describe various software used for criminal activity. Of all the websites we assist following a breach, over 90% had malware introduced into their website. Typically, malware is used to:
- Provide a back door for later access
- Load up other malicious software
- Enable stealthy reconnaissance
- Steal credit card data
- Provide interactive access for the attackers
- Steal personal data
- All of the above
Some malware is detectable using an external scan, however most of the malware that we encounter is well hidden. Some malware is able to evade detection from even the most vigilant website administrators. We advise that you scan your website for malware daily, using advanced malware detection tools.
Our solution, FGX-Web, is one of the most comprehensive available. You can read more about it here.
10. Use secure passwords at every step
It’s not uncommon for passwords to be guessed, once they are, websites are completely vulnerable to whatever the attacker has in mind.
A study carried out by mobile identity company TeleSign, has uncovered some scary statistics surrounding passwords. Their findings showed that 47% of people use passwords that are at least 5 years old. Even more shocking, 21% of people surveyed used passwords that were over 10 years old.
The importance of using a complex password cannot be understated. It only takes a few seconds to create a complicated password and it could potentially save your business tens of thousands of pounds. The five most popular passwords used in 2014 were:
- 123456
- password
- 12345
- 12345678
- qwerty
I don’t think I need to tell you that using one of the above-mentioned passwords isn't a smart move. Businesses need to be taking the time to empower and train employees, giving them the ability to recognise threats and protect against them.
Create a complex password
Use a password that contains both upper-case and lower-case letters, alongside numbers or special characters such as question marks or full stops. It’s advised that you avoid using dates, dictionary words, or any information that’s relevant to yourself like a pets name or home town.
Make sure your password is unique
Everybody is busy in todays world and using the same password for all of your logins may seem like a convenient time saving device. In reality, it can have detrimental ramifications. It only takes your password to be guessed on one service, then a hacker has access to all of your accounts and all of the data stored within them.
Do not keep your password saved on your PC
Keeping your password saved on your computer is not a wise option when we’re talking security. There’s new malware being created every day and if your PC were to be infected, it could leave your eCommerce website password exposed. Alongside any other personal information you might have stashed away.
11. Implement multi-factor authentication
Multi-factor authentication provides an extra layer of security and makes it harder for attackers to gain access to a person’s device or online account. This is because knowing the victim’s password would not be enough to gain access. With multi-factor authentication, an attacker would need multiple pieces of information. There are several different types of authentication factors:
Knowledge factors:
This is something only the legitimate user would know, such as a PIN or personal information. Knowledge factors are the most common category of credentials used for authentication.
Possession factors:
Something the legitimate user has, such as an ID card, security token, or smartphone authorisation.
Inherence factors:
Commonly called biometrics, they usually include personal attributes such as fingerprints, your voice, or iris scan.
Single factor passwords are at risk of being exploited by external threats such as brute force attacks, dictionary or rainbow table.
I hope you’ve found these tips useful. As a final piece of advice, I would say to check your website and make sure you have the means in place to prevent an attack. Having something like a WAF in place can be the difference between a successful online business and a business crippled by expensive fines, reputational damage and loss of custom.
If you'd like to know more about how we can help you protect your website, click the link below!
Subscribe to our Blog