Subscribe to our Blog
It even has functionality to add a further backdoor onto the system which would allow the attacker to connect back to the server as desired. The malware, named ‘BArNEr’ within the code, appears to be present on a number of systems in the wild and may be connected to an Indonesian cyber crime collective called the ‘Indonesia HackRs’.
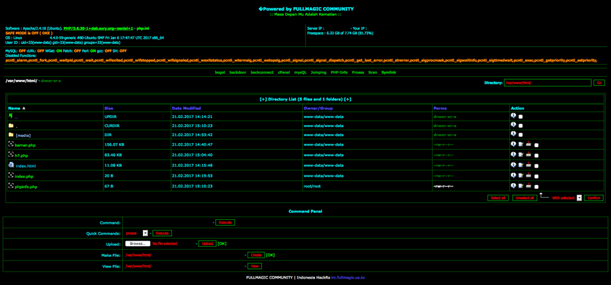
The code that creates the web shell is generally found “hidden” at the end of a JPEG image.
Known as a ‘dropper’, this file would first be placed on a compromised system and then activated by the attacker requesting it from the website. During analysis it was found that the code for the web shell did not work on PHP 7 (due to its use of a depreciated function) but would function as intended if the affected website was running PHP5.
Foregenix urges website owners to examine their systems for presence of this malware.
How do I detect this malware on my website?
 Detection is simple with the right tools. Apply for a Website Health Check of your site and our team will scan the internal file system of your environment using FGX-Web for this malware and many others.
Detection is simple with the right tools. Apply for a Website Health Check of your site and our team will scan the internal file system of your environment using FGX-Web for this malware and many others.
Alternatively, the following grep commands should reveal these files if they are present:
Ajax Harvester – Initialiser
|
grep -slr‘\\x6F\\x6E\\x65\\x70\\x61\\x67\\x65\\x7C\\x63\\x68\\ x65\\x63\\x6B\\x6F\\x75\\x74\\x7C\\x6F\\x6E\\x65\\x73\\x74\\x65\\ x70\\x7C\\x66\\x69\\x72\\x65\\x63\\x68\\x65\\x63\\x6B\\x6F\\x75\\x74’ . |
Ajax Harvester – Harvester
|
grep –slr‘\\x73\\x65\\x6C\\x65\\x63\\x74\\x5B\\x69\\x64\\x3D\\x22\\x73\\ x74\\x72\\x69\\x70\\x65\\x43\\x61\\x72\\x64\\x45\\x78\\x70\\x69\\x72\\ x79\\x59\\x65\\x61\\x72\\x22\\x5D’ . |
Webshell Dropper
|
grep -slrR 'file_exists\|BADUBAMM' . |
‘BArNEr’ Webshell
|
grep -slr '7P15f9s4kjgO/737+ex7YDSejj12rNOH4o6nqfs+rTOdn4ciKYoSJcqk7t' . |
