Subscribe to our Blog
Obfuscated Website Modification Code – The new “average” attack
The prevalence of this type of site modification has meant the code seldom gets a second look by our team – it is simply decoded, classified and recorded. Following this, we quickly update our FGX-Web solution to automate protection for other clients. Even the classification is generally a straight forward operation as the malware usually fits into one of a few groups. Indeed, the volume of website compromises recently has been unprecedented, with popular development frameworks having serious vulnerabilities publicised and insecure implementations increasingly common.
Recently though, a few investigations have identified a different calibre of obfuscated code. The presence of the code is often hidden in plain sight, relying on the automatic capability of certain editors to ‘collapse’ or skip over comments, or the natural urge of users to ignore the norm and proceed directly to the task at hand.
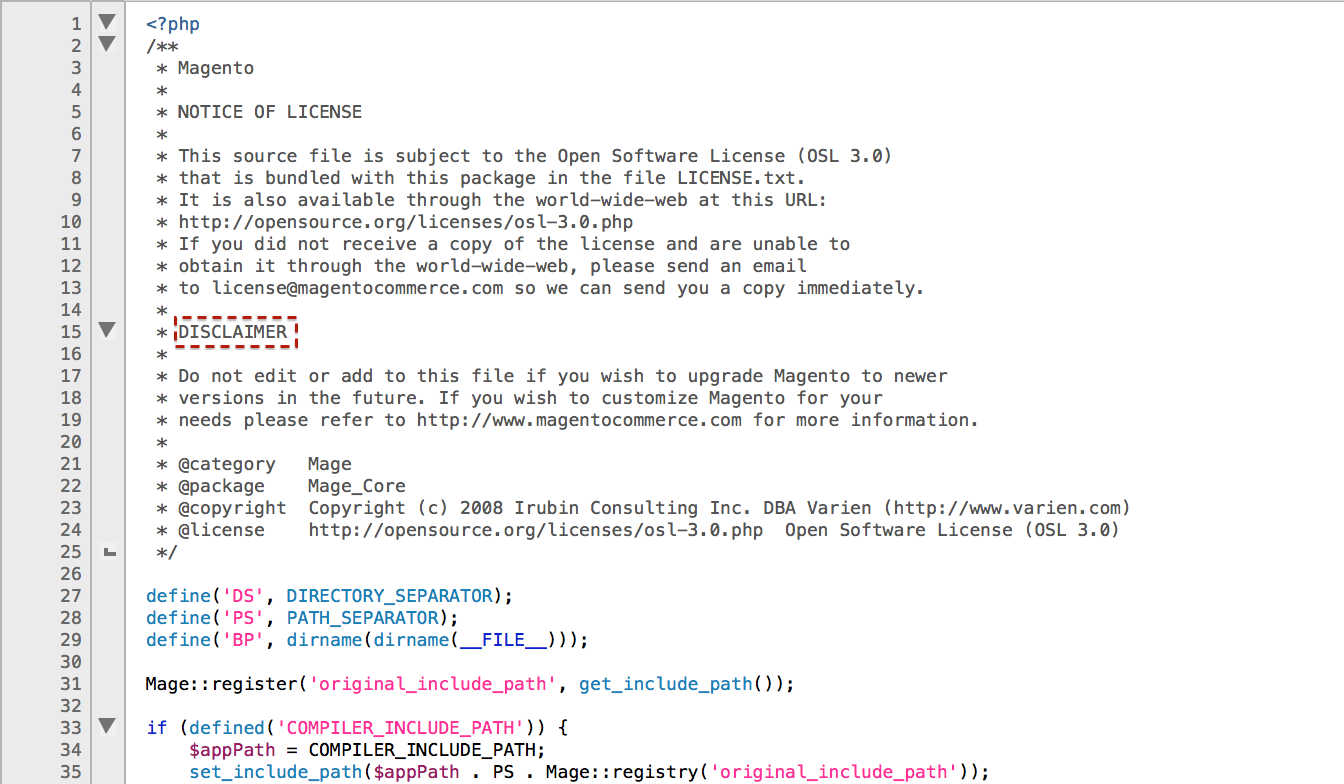
The following image shows the modified file open in a popular text editor. On the face of it nothing seems out of the ordinary and the Magento comments at the top of the file seem perfectly normal.
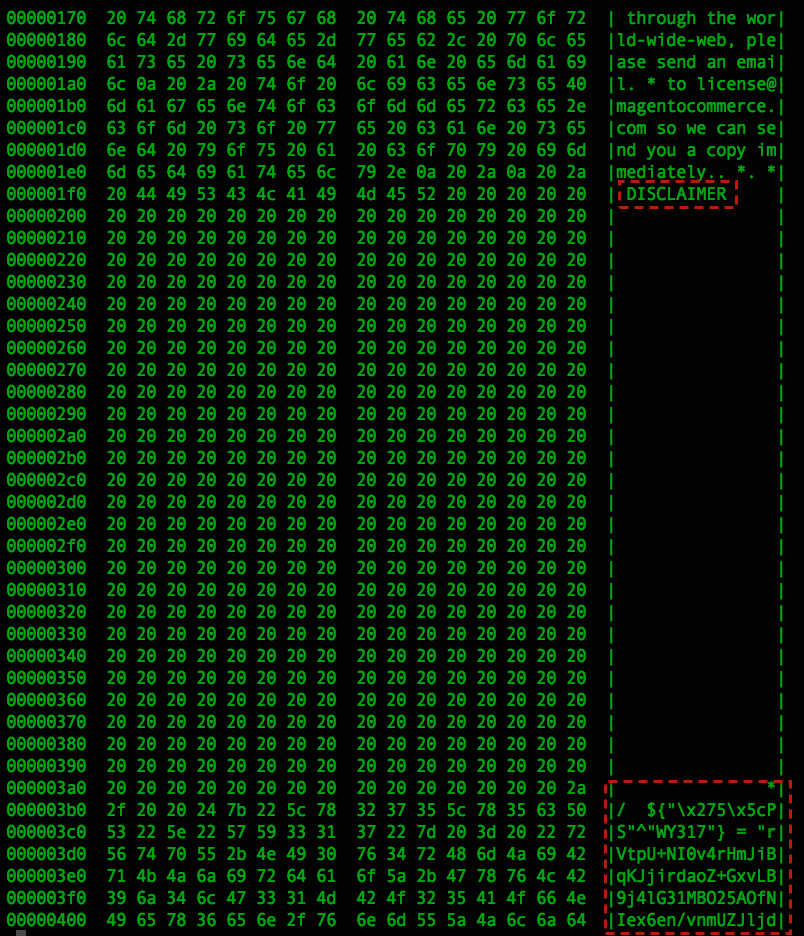
This next image shows the same file “dumped” showing the hexadecimal value of the file’s contents along side the ASCII representation of the characters. You can see the “DISCLAIMER” text highlighted in both images. Note the additional characters highlighted at the bottom of the hex dump though. This is the malicious code which has been appended to the DISCLAIMER line of text, with several intervening spaces. This ensures the modification is “out of sight” of the majority of tools.
The script uses several layers of encoding (binary XOR and text based base64), compression and function lookup tables to protect or hide the internal workings of the malware. The approach the attackers take makes it extremely easy to change the outer layers, thereby making it more difficult to detect in an automatic fashion, although it certainly is possible.
When all the obfuscation layers are stripped away, we’re left with a novel theme on the payment card harvesting attacks. Where as it is fairly common to find the compromised data appended to an image file, making it easy to anonymously download - or email the compromised data to a temporary email address - this malware actually encrypts the payment details and puts it back in the local database.
That’s right, the attackers are now hiding the compromised details in your own database.
The malware provides facilities to manage the table that the payment information is being saved to and also allows the attackers to download the data and purge the data as and when they deem it necessary.
Although it is trivial for the attackers to modify the code and use arbitrary table names, we have seen minor variations on the name ‘catalog_product_index_price_tmp_idx’ being used.
Website owners and web developers are strongly advised to regularly review their databases, checking for unusual or new tables that may be present. Obviously, regularly and frequently reviewing the source of your site is also beneficial to detect compromised or modified files.
How can you defend against these types of attacks?
While this is a very clever attack, its actually very easy to protect a website from this kind of attack - these are the steps we would recommend:
- Place a tamper-proof seal on your website to alert you to any changes being made on the website. If you see changes and they are yours, that’s fine. If you see changes and they are not yours, you need to act quickly as it is likely an attacker.
- Check for Malware/Web Shells daily.
- Collect and analyse your log data daily.
- Check your website for unprotected credit card data - if an attacker is collecting data, they usually store it somewhere on the website for later collection/exfiltration.
- Use a hosted payment page to further protect your client payment card data.
Do you need help?
If you do find anything out of the ordinary and require assistance, drop and email through to support@foregenix.com - we’d be happy to help.
If these manual reviews are too time consuming and you’re looking for an automatic cost effective service to do it for you – as well as perform all the automated protective checks listed above - have a look at our FGX-Web product at www.foregenix.com/fgxweb.php
You can even use the tool free for 7 days to scan your website for malware or suspicious activity:
Learn more about website security
- Download our Magento Phantom Malware Technical Whitepaper
- Watch our Webinars - Baking Web Security into Web Development
- Read our Blog: Webiste Redirect Payments... Secure or not?